I’ve talked a lot about how I no longer do “fuzzy mentorship.” (If you haven’t heard the term, it’s generally seen as mentorship that focuses mostly on vague things like good vibes and is endeavored upon mostly for reasons of…
A Year of Reading Only New Things
It was March 4th, 2022. I already re-read all my comfort books over the last two years. In an effort to avoid becoming dull-witted, I’m going to only read new things for a year, between March 4th, 2022 and March…
An education-based approach to curbing CSAM production
Originally published in Brookings TechStream. March 17, 2022 Savannah Sly and Tarah Wheeler In recent weeks, a misguided legislative initiative to provide children with better protection online has gained momentum on Capitol Hill. In its current form, the Eliminating Abusive and Rampant Neglect of Interactive Technologies…
4 Truths About Cybercrime (and the research to back them up)
Original post on Medium. I was recently asked by someone involved in policymaking for a short bulleted reading list on cybercrime and how to understand the major issues since they didn’t come from a technical background. I started writing the…
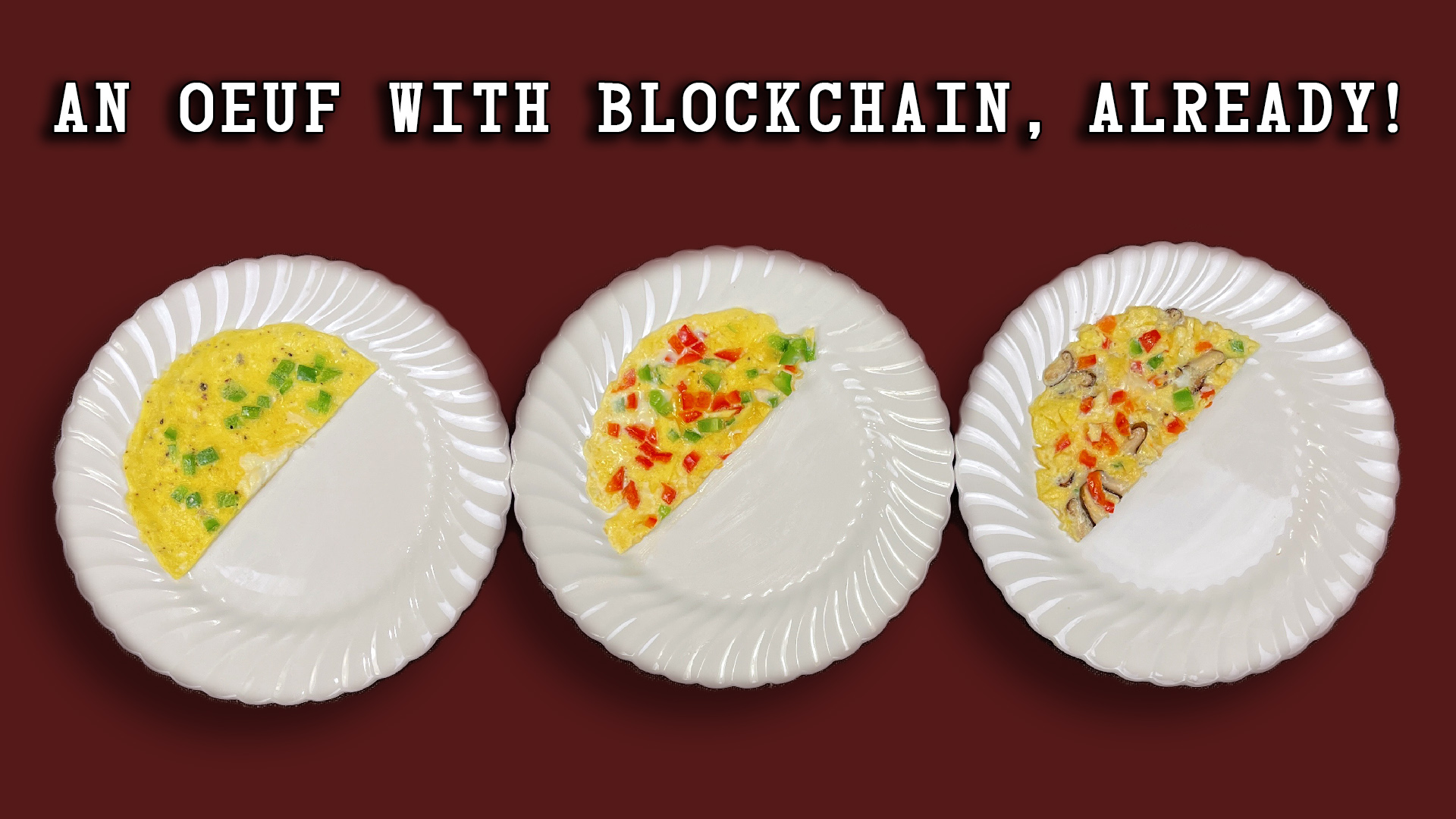
Blockchain Eggs
I created a short video and slide deck to help illustrate how a blockchain works. This is not about Bitcoin, but is intended to help people who aren’t as experienced with Merkle trees understand that the idea of a blockchain…
Where are the women in cybersecurity leadership roles?
This post originally appeared on the OECD Forum’s site. It’s easy to feel like everything has already been said about why we need more women in cybersecurity. I’ve been explaining the economic benefits of hiring women as engineers, bringing in…
NATO, We Want To Go To War With You
Originally on Foreign Policy, December 22nd, 2020. Wargames can provide essential cybersecurity training for soldiers. But they won’t succeed unless the players confront real, independent hackers. BY TARAH WHEELER, AMY ERTAN | DECEMBER 22, 2020, 7:53 AM In recent years, NATO has begun to…
The Lady of Shalott
I started this project when I was 19. I remember sitting on the lawn at Carroll College in Helena, Montana, and starting that first stitch up in the top left corner in DMC 420. The Lady of Shalott is a…
PKI — public key infrastructure, explained
(originally posted https://tisiphone.net/2018/03/07/the-infosec-amnesty-qa/ with thanks to Lesley “Hacks4Pancakes” Carhart) Here’s why I know about this My tech journey started in academia, where I spent my time writing math in Java. As I transitioned more and more to tech, I ended…
How much should startups spend on information security
When you have little to no budget, how do you start spending on information security in a startup to protect customer data and operations? I was asked to comment on this via email by Zack Whittaker for a story he was doing…